
David Lim • 4 minute read
FizzCore: A Growing Threat to Publishers’ Revenue and Audiences

Threat actors are malicious entities responsible for organizing and executing attacks that compromise the data of an individual or organization. In the world of programmatic advertising and digital publishing, new threat actors continuously emerge armed with advanced techniques and tactics to compromise data. Their immediate goal is to evade preventative measures that ad platforms and publishers implement to protect their audiences.
Confiant’s experience and expertise with threat intelligence inform our proactive approach to protecting our customers and the entire programmatic ad ecosystem. Case in point: Confiant tracked and researched the movement of a new threat actor that we identified as FizzCore. We then published the results of six months of research from August 2019 to January 2020. Publishers, ad platforms, and enterprises routinely use this intel to protect their audiences from this malicious but effective cryptocurrency scam.
FizzCore isn’t going anywhere anytime soon. We discovered these criminal ads targeting the UK in September, with ads surfacing in Germany and Italy in the following months. For now, FizzCore is focused on Europe because of the U.S.’s strict regulations surrounding cryptocurrency. However, FizzCore has inspired copycat threat actors around the globe who are testing and iterating new tactics to scam audiences, ultimately disrupting publishers’ revenue streams by damaging their trust, brand integrity, and reputation with audiences.
Blurring the Lines Between Malvertising and Deceptive Ads
How does FizzCore work? How has it been able to successfully evade traditional digital advertising QA mechanisms and reach millions of visitors? In short, they are a large scale affiliate with global reach, utilizing cloaked deceptive ads to maximize persistence and click-through rates.
How FizzCore scams audiences in three steps:
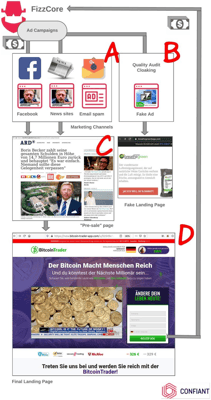
- FizzCore distributes ad creatives containing shocking imagery to popular news sites in Europe, showcasing a fake photo of an injured celebrity. Because the image plays on human emotion, these creatives drive a very high click-through rate.
- After clicking the ad, the user is taken to a fake news article that acts as a pre-sale landing page for the scam. This page details how the celebrity recommends a bitcoin investment, encouraging the user to click once more into the bitcoin landing page.
- Users submit their contact information on the bitcoin landing page and receive a phone call from a salesperson. They falsely explain how the investment will provide returns to the user. The user is often a retired person who loses their pension by sending wire transfers for hundreds of thousands of dollars and receiving nothing in return.
Why is FizzCore able to persist?
Some malicious advertisers can stay hidden for months or years because they employ strategies that allow them to remain unnoticed by ad platforms and publishers. FizzCore has taken the opposite approach, amping up its efforts as high as possible until they get caught. On a big day, we estimate that they can capture over $1M in just a single country. With such lucrative returns, FizzCore can justify rebuilding their infrastructure each week, coming back to similar platforms using similar techniques, running in some cases for only a few hours until being forced to shut down again after ad platforms identify the issue and stop the ads.
Cloaking techniques play a big part in FizzCore’s long-term success. Advertising platforms have restrictions on ad creatives to protect audiences, but malvertisers have found ways to identify and circumvent these screening efforts. Detection tools can identify artificial scanning environments by analyzing certain parameters of the device, such as battery life or accelerometer readings. If the malvertiser detects a scanner, they can submit a safe image that goes to a legitimate link and swap it out with the fake creative and link after the ad passes through the platform. This allows the malicious ad to remain on the publisher sites, often until a user complains.
FizzCore has built strong relationships with eight ad platforms in the first six months of our research, four of which are considered tier-one platforms. To appear more legitimate and foster these relationships, they also moved to three commercial ad servers to raise fewer red flags than the open-source servers they had used before.
To summarize, FizzCore has been extremely successful by combining heavy and fast attacks, celebrity-endorsement clickbait campaigns, sophisticated cloaking techniques, and strong relationships with ad platforms and ad servers.
How FizzCore is inspiring a new generation of malvertisers
 Confiant is noticing more and more threat actors using similar techniques on a weekly basis. The process is dangerously efficient; register as an affiliate with the cybercriminals, build your ad campaign with creatives supplied by the operator, employ cloaking methods to run ads undetected, host a landing page with pre-sale page content provided by the operator, send traffic to the bitcoin landing page, and reassess your techniques and iterate. New threat actors are executing these loops, learning as they go, and iterating to improve their chances of success.
Confiant is noticing more and more threat actors using similar techniques on a weekly basis. The process is dangerously efficient; register as an affiliate with the cybercriminals, build your ad campaign with creatives supplied by the operator, employ cloaking methods to run ads undetected, host a landing page with pre-sale page content provided by the operator, send traffic to the bitcoin landing page, and reassess your techniques and iterate. New threat actors are executing these loops, learning as they go, and iterating to improve their chances of success.
As word spreads about the success of bitcoin campaigns using celebrities, threat actors who previously employed other techniques are moving to bitcoin scams with similar creatives and are finding success. Some have integrated celebrity ads into other types of campaigns. And some threat actors have found success without cloaking by sending ads through less scrupulous ad platforms.
Protect your audiences from bad ads with Confiant’s unique and effective approach
FizzCore presents three significant challenges for ad platforms and publishers who need to protect their audiences: sophisticated ad cloaking, a constant flux of threat actors and techniques, and an explosion in the number of threat actors following the FizzCore “recipe” while making incremental improvements.
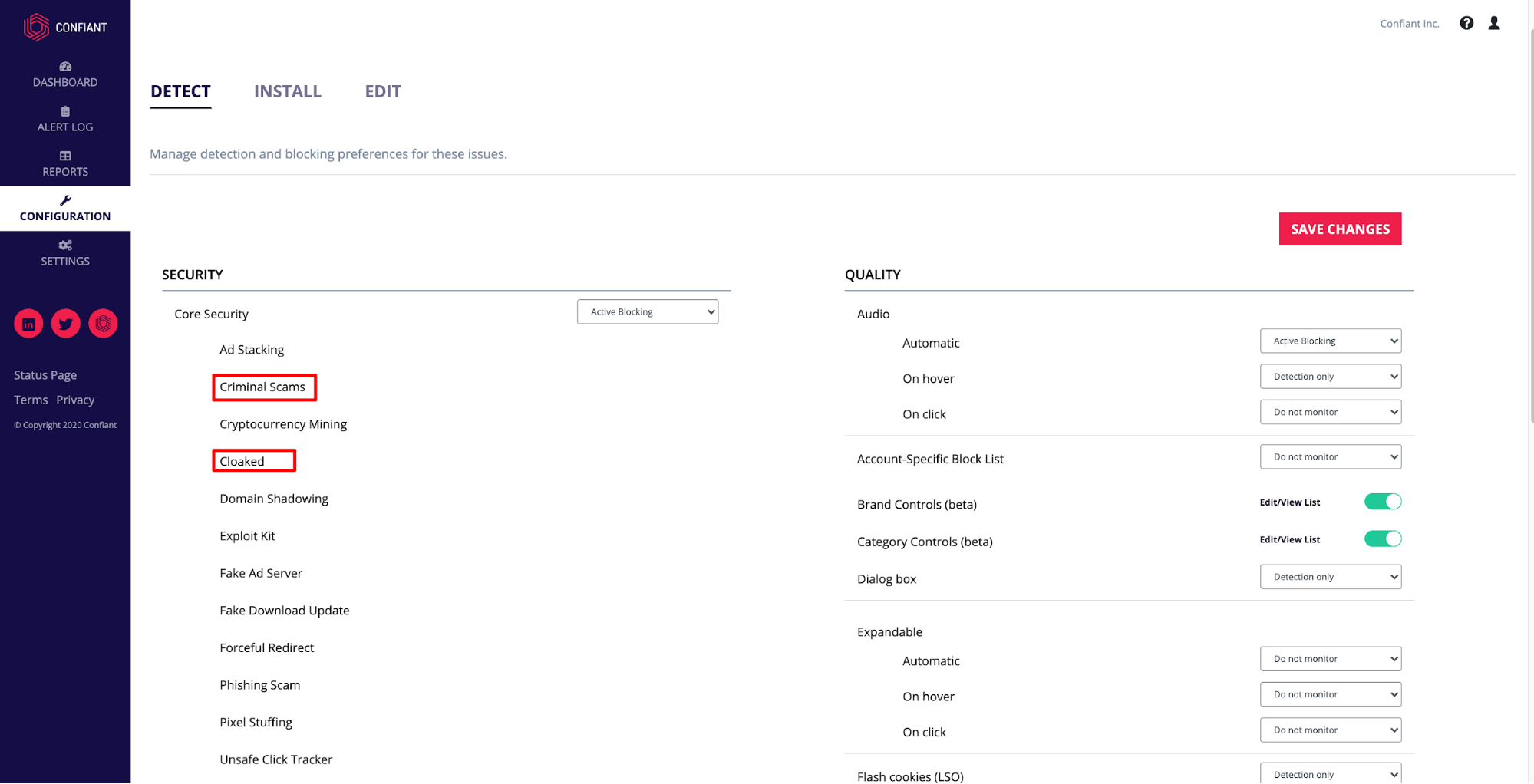
To combat cloaking, Confiant combines the inspection of the ad creative, in addition to client-side telemetry. Our code runs on the client’s page and inspects the creative as it loads for a real user. Combining these two techniques means we can identify cloaking and gain full visibility into the attacker’s objectives. Publishers that use our platform can find this type of threat in their dashboard and alert log categorized as “Criminal Scams” and “cloaked” ads.
Our philosophy of focusing on the attacker, rather than categorizing each attack, helps us to stay ahead of threats. As we find a new attacker, we identify their tactics, techniques, and patterns to create a comprehensive threat profile that may include technical components and the mapping of their infrastructure. This allows us to keep track of their movements and prepare for their next moves, ensuring that we empower our customers to project their audiences. Confiant also works with other security teams from various companies to stop attackers and help law enforcement with malvertising cases. The ad ecosystem can only thrive when audiences have trust in the content delivered by publishers.
For more information on FizzCore and other active threat actors, in addition to SSP rankings and industry trends, download Confiant’s latest Demand Quality Report. Or, if you are ready to put Confiant to the test, request a free trial of Confiant’s Ad Security & Quality solution.




